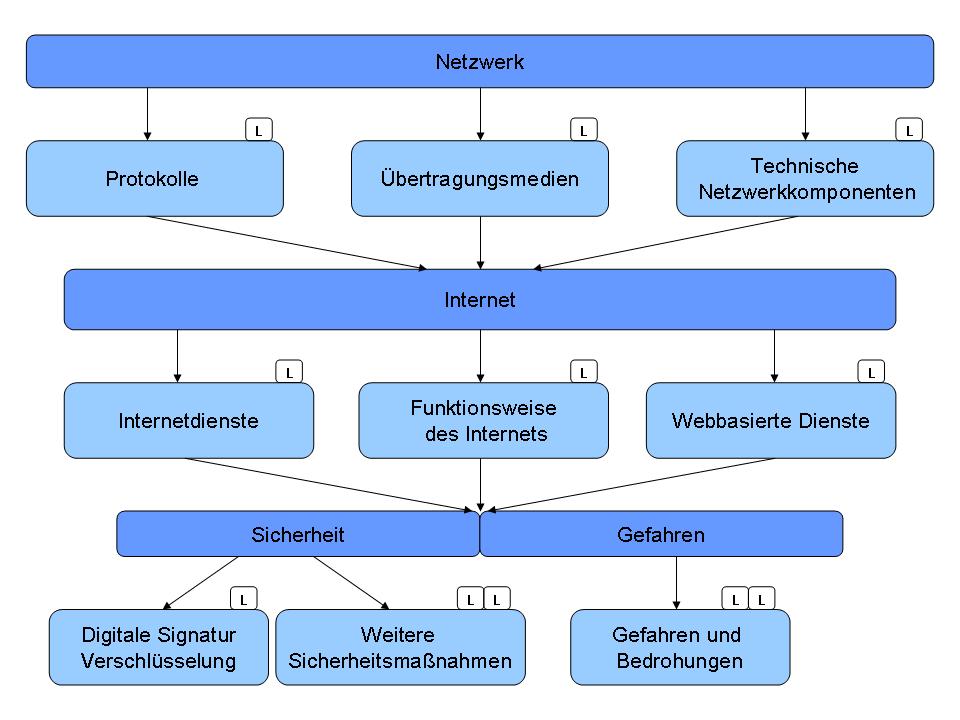
Vertiefung Technische Grundlagen
<map id="imgmap2009525134728" name="imgmap2009525134728"><area shape="rect" alt="1" title="" coords="24,32,932,86" href="" target="" /><area shape="rect" alt="" title="" coords="24,138,282,212" href="" target="" /><area shape="rect" alt="1b" title="" coords="352,142,604,212" href="" target="" /><area shape="rect" alt="1c" title="" coords="672,138,932,212" href="" target="" /><area shape="rect" alt="2" title="" coords="62,268,892,328" href="" target="" /><area shape="rect" alt="2a" title="" coords="62,380,310,454" href="" target="" /><area shape="rect" alt="2b" title="" coords="356,382,604,454" href="" target="" /><area shape="rect" alt="2c" title="" coords="646,382,894,454" href="" target="" /><area shape="rect" alt="3" title="" coords="116,510,476,552" href="" target="" /><area shape="rect" alt="3a" title="" coords="48,608,264,682" href="" target="" /><area shape="rect" alt="3b" title="" coords="274,610,524,682" href="" target="" /><area shape="rect" alt="4" title="" coords="478,508,840,552" href="" target="" /><area shape="rect" alt="4a" title="" coords="572,608,786,682" href="" target="" /></map>